Layers – Not just for Onions and Ogres
Security has been thought of and taught to others as a “layered approach” for centuries, and as such is not a new concept. The Romans used layered concepts in their infantry tactics as well as their defensive fortifications. With all due respect to “Shrek“, security is like an onion, and is a complex layer of countermeasures that make up a suite of hurdles that, presumably, are so confounding or problematic that the opponent gives up, gets caught, or never attempts anything in the first place.
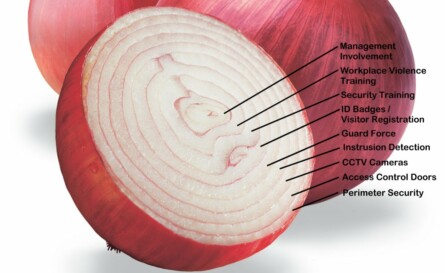
Layers of security are a simple concept, but the concept is often overused by security professionals in discussion and even trivialized as not very important. As Americans, we tend to rely very heavily on technology. We understand technology, and we’re pretty good at it. But while having thermal night vision cameras, fiber optic sensing cables, and CCTV drones flying over your campus are an impressive security posture, sometimes just a plain old chain link fence or dense thornbush hedge are enough to deter the would be criminal. The most effective barrier I ever saw was a dense hedge of thorns called a “living wall”. It was 6 feet tall (and still growing), and you couldn’t climb it, cut it, or burn through it.
We once worked with a client that had installed a $4500.00 bullet proof door with a card access proximity reader installed behind Lexan (to protect it too) on the wall. It we very impressive, until we learned that the wall it was installed in was only sheetrock and metal studs, and you could kick through it and completely bypass the door.
Security layers mean from the outside in, with each layer adding to the increased security profile. But security profiles are different for different companies, buildings, or campuses. It depends upon the corporate philosophy, culture, and threat profile. What may be reasonable for a chemical company manufacturing DOD explosives may not be suitable for a quarry.
Start with the outside, what are the threats from the street, the site perimeter, or even from the air? Then work to the building perimeter, where are points of entry, access control weaknesses, or blind spots? Internally you should look at the lobbies, common areas, break rooms, stairwells, and vestibules. Then finally to policies and procedures relating to security, safety, and employee awareness. Each of these areas will generate questions, to which you should generate answers in the forms of layers of security to add to your security profile.
Posted in: CPTED, Security Consulting
Leave a Comment (0) ↓