NSA Releases Guidance on How to Protect Against Software Memory Safety Issues
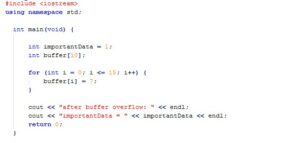
When the NSA makes a post about software best practices to reduce hacking attempts, you know there’s a problem. For the non-programmers, a memory safe programming language is one that has built-in features to reduce or eliminate the possibility of a poorly crafted program to be exploited (usually by malicious input) by causing a memory buffer overrun or similar failure that can corrupt data, run a malicious payload, or escalate privileges. These problems have been around for years, and there are several programming languages that are common offenders (C and C++), but are ubiquitous and have long codebase history that makes it unattractive to rewrite.
Fortunately there are quite a few memory safe programming languages to choose from, such as C#, Go, Java, Ruby, Rust, and Swift. Of course it’s not enough to just change programming languages, good security coding practices, hardening tools, safe compiler options, and thorough testing should also be used as well.
For the NSA full article, click here: https://www.nsa.gov/Press-Room/News-Highlights/Article/Article/3215760/nsa-releases-guidance-on-how-to-protect-against-software-memory-safety-issues/
Posted in: Company News
Leave a Comment (0) ↓